A technical configuration file from The New York Times website has been inadvertently exposed, revealing internal system parameters and security protocols typically hidden from public view. The exposed data appears to be part of a CAPTCHA delivery system configuration, containing various technical identifiers and encrypted hash values that are normally used for website security and user verification processes. The configuration includes a complex array of technical parameters including routing information marked as 'rt':'c', along with multiple identification codes and hash values such as '499AE34129FA4E4FABC31582C3075D'. The exposed file shows connections to geo.captcha-delivery.com, a service commonly used by major websites to prevent automated bot traffic and ensure legitimate user access. The technical data includes cookie information and encrypted strings that are typically part of the backend infrastructure supporting the newspaper's digital platform. While such exposures are generally not considered major security breaches, they do provide insight into the technical architecture that powers one of America's most prominent news websites. The configuration data suggests sophisticated security measures are in place, including geographic-based CAPTCHA delivery systems and multiple layers of user verification. Technical experts note that such backend configuration data is normally shielded from public access through proper server configuration and security protocols. The exposed information includes session identifiers, host routing information, and encrypted token values that facilitate secure user interactions with the website's content management and delivery systems.
- Who Is the Artist?
- Robots Are No Longer Workers. They Are Becoming Mirrors.
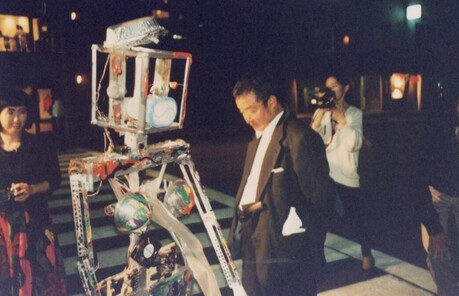
- Nam June Paik’s “Robot K-456” Has Returned to the Stage, Decades After Its Last Steps
- National Museum of Korea to Extend Hours, Add Outdoor Facilities to Ease Visitor Congestion
- K-pop Wins First Grammy as Global Music Landscape Shifts
- BTS Returns as a Full Group, Signaling a New Global Phase with Album, World Tour, and Industry Impact
- Eva Zucker Unveils Four New Works from “Menschsein in Schichten,” Announces 2026 Open-Studio Participation
- The Price of Silence