A technical code fragment has been discovered on the New York Times website, revealing backend security and tracking mechanisms used by the publication. The code snippet contains various technical parameters including runtime configurations, client identification numbers, hash values, and security tokens. The fragment shows a variable declaration with multiple data points: a runtime type marked as 'c', a client ID string 'AHrlqAAAAAMAvAEsEb9w-s8AeVgFqA', and a hash value '499AE34129FA4E4FABC31582C3075D'. The code also includes a session size parameter of 17,439 bytes and references to geo-location captcha delivery systems hosted at 'geo.captcha-delivery.com'. Additionally, the fragment contains an encrypted security token and cookie data used for user session management and authentication purposes. This type of code is typically used by major news websites to manage user interactions, prevent automated access, and ensure secure content delivery. The presence of such technical elements highlights the complex infrastructure required to operate a major digital news platform like the New York Times, where security measures and user tracking systems work together to maintain site functionality and protect against unauthorized access.
- Who Is the Artist?
- Robots Are No Longer Workers. They Are Becoming Mirrors.
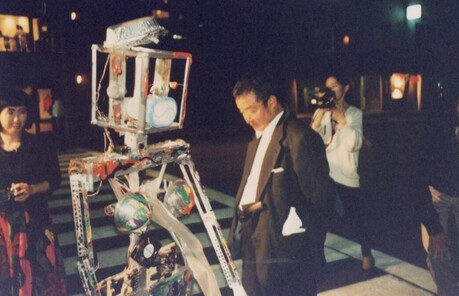
- Nam June Paik’s “Robot K-456” Has Returned to the Stage, Decades After Its Last Steps
- National Museum of Korea to Extend Hours, Add Outdoor Facilities to Ease Visitor Congestion
- K-pop Wins First Grammy as Global Music Landscape Shifts
- BTS Returns as a Full Group, Signaling a New Global Phase with Album, World Tour, and Industry Impact
- Eva Zucker Unveils Four New Works from “Menschsein in Schichten,” Announces 2026 Open-Studio Participation
- The Price of Silence